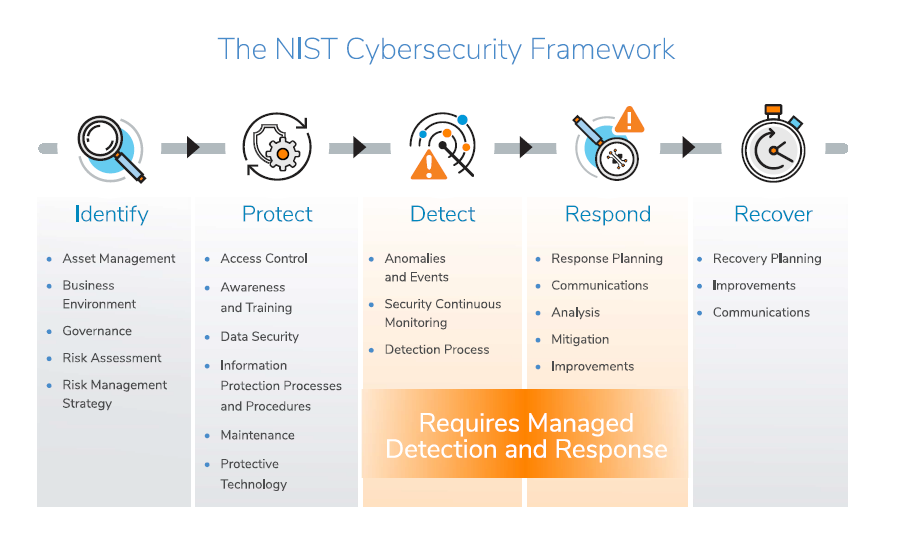
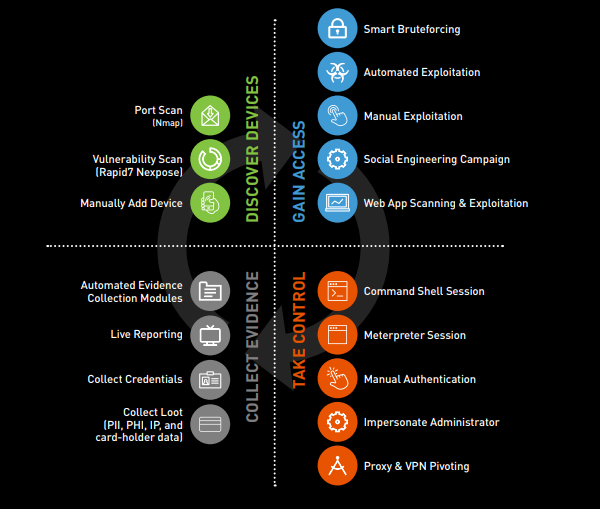
Unfortunately, new software vulnerabilities are discovered on a daily basis.
Vulnerability management (VM) is the means of detecting, removing and controlling the inherent risk of vulnerabilities. The vulnerability management program utilizes specialized software and workflow to help eliminate detected risks.
External or internal vulnerability scans are conducted as part of a regular cybersecurity risk assessment to assess your company’s security posture. We works with you every step of the way to develop a plan to address the most critical weaknesses and provide insights into the best way to remediate.
We perform results analysis that combines the latest threat intelligence with a deep understanding of your critical assets to develop an accurate list of your current vulnerabilities.
A Risk-based and priority remediation report will be shared with your team including recommendations to limit exposure and remediate most important weakness faster.
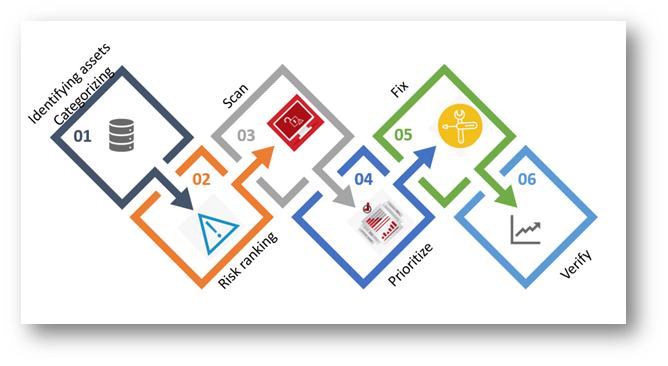
Vulnerabilities Management life cycle :
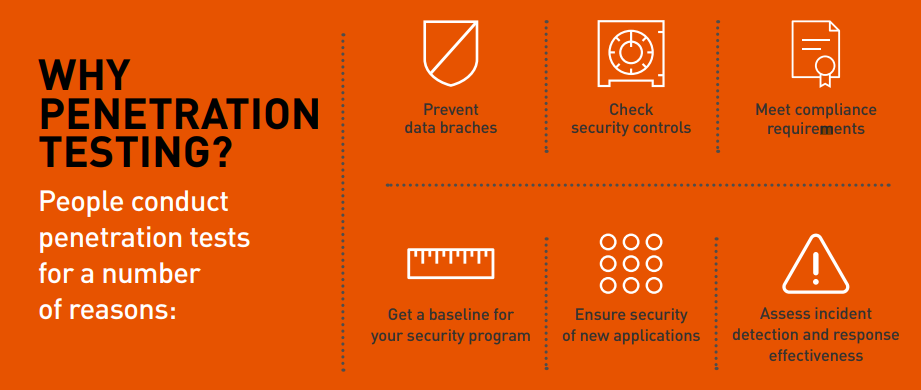
PENETRATION TESTING
Penetration testing is the process of identifying security gaps in your IT infrastructure by mimicking real world attacks. Think about it as quality assurance for your IT security.
Rapid deployment: SOC-as-a-service in 60 minutes.
We offer cloud-based security operations center (SOC) available as an affordable monthly subscription service. The deployment is simple and starts with senors installed in your network. The sensors immediately starts gathering machine data and sending, where it is analyzed in real time.
It only take few minutes to start security operations in your network.Protect your IT and business We combines human and machine intelligence to analyze millions of events in real-time for 24×7 threat detection. We correlate security events from all infrastructure, security devices and applications before delivering events to your designated Account Engineer to review and respond to in seconds. If a threat is detected, we notifies you with details, analysis and recommended remediation for incident response. This not only helps protect your organization from a data breach, but also saves valuable time for your IT and security teamsSecurity experts to augment your IT team You get a dedicated security engineer who is working in a 24×7 SOC with the whole team to monitor your network and analyze your security events so threats are detected in real time.
Compliance and security have more than half of their policies in common. Compliance is usually a byproduct of a best security practice. Typical compliance policies are about data privacy, log collection, log storage, vulnerability management, encryption, firewall, network equipment configuration, access control, network mapping and others. We covers the majority of compliance policies, ISO, PCI, HIPAA etc…There’s no need for large team management, costly training and security solutions, our team is already there to help you and secure your network in few minutes.
End point Security as a Service
Traditionally endpoint security is a centralized solution, running on a server or an on-premises appliance, requiring direct management from your IT security team. In the early days of endpoint security, these solutions usually only meant installing an anti-malware on your endpoints and forgetting about them. SaaS-based endpoint security, on the other hand, allows your enterprise to free up your IT security team’s schedules and responsibilities.
SaaS-based endpoint security is similar to traditional endpoint security: it protects your IT environment perimeter from anti-malware and ransomware, deploys endpoint detection and response (EDR), and initiates data loss prevention measures.
However, SaaS-based endpoint security offers full-time protection even as your enterprise scales upward. These solutions allow your IT security team to maintain your perimeter even as it encompasses multiple endpoints and remote mobile devices; this meets the new requirements of employees working from anywhere for their enterprise. SaaS-based endpoint security also serves to protect against more advanced malware and persistent threats, traditional endpoint security solutions can’t do that.
Free you IT team, no need for dedicated team to manage your dedicated solution, reduce your cost Benefits:
> Threat Intelligence, real time feed
> 24×7 alerting for continuous monitoring
> Customized security policies
> Reporting